Effective cybersecurity isn't about buying a single piece of software and calling it a day. It’s about building a multi-layered defense strategy, almost like the layers of an onion. For small to midsize businesses, this approach must be smart and efficient, weaving together crucial elements like firewalls, AI-powered threat detection, secure cloud solutions, and robust employee training to protect what really matters: your client data, financial records, and intellectual property.
Why Your Business Needs a Cybersecurity Strategy Now
Staring at the endless list of digital threats can feel paralyzing, but looking the other way is a luxury no business can afford anymore. Cybersecurity has officially moved out of the IT closet and into the boardroom. It's a core business function, just as critical as sales or operations, especially for SMBs leveraging AI and cloud technologies.
Think of your company’s digital assets—customer lists, financial statements, proprietary designs—as your most valuable inventory. Leaving them unprotected is like leaving your storefront unlocked overnight with the cash register wide open. It’s just not an option.
This is especially true for small and midsize businesses (SMBs), which have become the new favorite target for cybercriminals. Attackers see smaller companies as low-hanging fruit, assuming (often correctly) that they lack the sophisticated defenses of a Fortune 500 corporation. A successful attack can trigger a devastating chain reaction that goes far beyond a simple financial hit.
The True Cost of a Security Breach
When a breach happens, the damage isn't contained to one department. It ripples through the entire organization, hitting your finances, your operations, and your reputation all at once.
-
Financial Damage: This is the most obvious one. It includes the direct costs of fixing the mess, steep regulatory fines if you're found non-compliant, and the potential for lawsuits.
-
Operational Disruption: Suddenly, you can't access your cloud services, serve customers, or process orders. Downtime brings your entire business to a grinding halt.
-
Reputation and Trust: This is the cost that can linger the longest. Customer trust is incredibly hard to build and frighteningly easy to lose. A public data breach can permanently tarnish your brand, sending customers right into the arms of your competitors.
Building a proactive security plan is a direct investment in your company’s reputation, customer loyalty, and long-term survival. It sends a clear signal that you take the responsibility of protecting people's information seriously. For a deeper dive into the fundamentals, our introduction to cybersecurity for small businesses is a fantastic place to start.
The explosive growth of the global cybersecurity market tells the story. In 2023, the market was valued at a staggering $190.4 billion, with some forecasts predicting it will blow past $300 billion by 2025. That kind of money isn't being spent on a whim; it’s a direct response to how dangerous the digital world has become. To build a defense that actually works, you need to understand what you're up against. Exploring the top cybersecurity solutions for small businesses will give you a good sense of how modern tools are designed to counter today's threats.
Building Your Digital Fortress Layer by Layer
Good cybersecurity isn’t about finding a single magic tool that solves everything. I've seen too many small businesses try that approach, and it never ends well. Instead, the strongest defense relies on a multi-layered system, where each part acts like a specialized guard with a very specific job. It's an approach we call "defense-in-depth," and it ensures that if one layer gets breached, another is already in place to stop the threat cold.
Think of your business like a medieval castle. You wouldn't just build a tall wall and call it a day, right? You’d have a moat, guards on the towers, and patrols walking the courtyard. Each element works together to create a defense that’s tough to crack. Your digital security should be built the exact same way.
The infographic below really drives home how a solid cybersecurity strategy is the foundation for everything you've worked to build—from your critical data to the reputation you have with your customers.
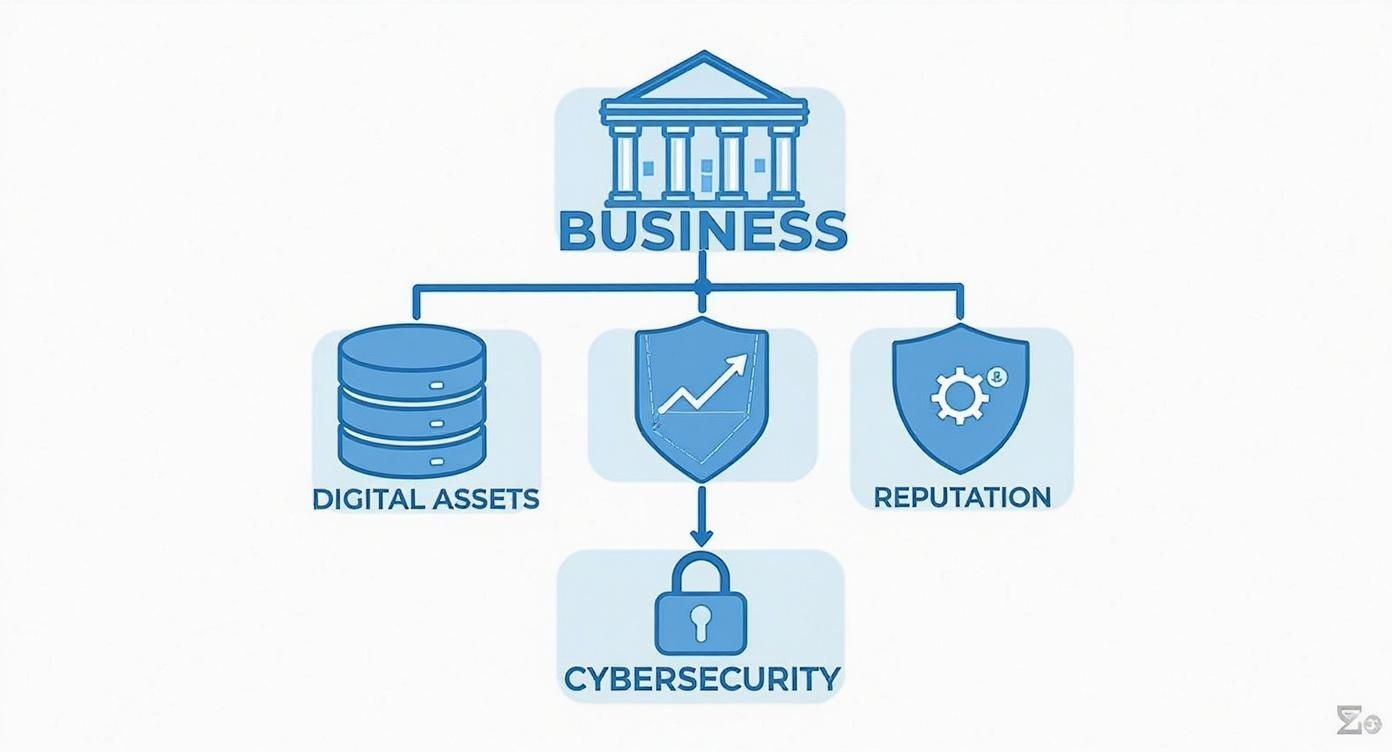
As you can see, a strong security posture isn't just an IT expense; it's what holds up your entire operation. Let's break down the essential layers you need to build that foundation.
Core Components of a Modern Cybersecurity Defense
To truly protect a small or midsize business today, you need a mix of technologies and strategies working in concert. Each piece has a unique role, and missing even one can leave a gaping hole for attackers to exploit. I've put together a table to simplify what these core components do and why they are absolutely non-negotiable for any modern SMB.
| Defense Layer | Primary Function | Simplified Analogy | Why It Is Critical Today |
|---|---|---|---|
| Firewall | Filters all incoming and outgoing network traffic, blocking malicious connections. | A security guard at the main gate of your property, checking every person and package. | This is your first line of defense. Without it, your network is wide open to the internet. |
| AI-Powered EDR | Monitors all devices for suspicious behavior using AI and can isolate threats automatically. | Elite security patrols inside your property, actively looking for intruders who slipped past the gate. | Traditional antivirus is no longer enough. AI-powered EDR stops modern threats like ransomware before they spread. |
| Cloud Security (CSPM) | Scans your cloud solutions (like Microsoft 365) for misconfigurations and vulnerabilities. | An automated compliance officer for your cloud, ensuring all doors and windows are locked. | A shocking number of data breaches start with a simple, preventable cloud misconfiguration. |
| Backups | Creates secure, isolated copies of your critical data so it can be restored after an incident. | An off-site, fireproof vault containing copies of your most important documents. | If ransomware hits, a reliable backup is often the only thing that can get you back in business. |
| Policies & Training | Educates your team on how to spot threats and establishes clear security rules. | The training and rulebook for your entire security team, ensuring everyone knows their role. | The human element is involved in over 82% of breaches. AI and cloud tools alone can't fix that. |
Having these layers in place transforms your security from a simple wall into a deep, resilient fortress. It's the difference between hoping for the best and being prepared for the worst.
The Perimeter: Your First Line of Defense
The first and most fundamental layer is your network perimeter. This is the digital border separating your internal business network from the Wild West of the public internet. The main tool for guarding this border is a Next-Generation Firewall (NGFW).
Think of an NGFW as a highly intelligent security guard at your company's front gate. It doesn’t just check IDs; it inspects the contents of every vehicle coming in and going out, hunting for anything suspicious. It controls all this traffic based on security rules we define, effectively shutting down unauthorized access attempts before they can even sniff around your internal systems. To really dig into this, you can learn more about why a firewall is crucial for your business in our detailed guide.
Protecting Your Endpoints with AI
Once traffic makes it past the firewall, it has to land somewhere. That "somewhere" is one of your company's devices—laptops, desktops, servers, even mobile phones. We call these endpoints, and they are hands-down one of the most common targets for attackers.
This is where AI-driven Endpoint Detection and Response (EDR) steps in. If the firewall is your gate guard, a modern, AI-powered EDR solution is the elite security team actively patrolling inside the castle walls.
Traditional antivirus software is like a guard with a binder of known troublemakers' photos. It's decent, but what about a new threat? Modern EDR, powered by AI, analyzes behavior. It spots suspicious activity even from brand-new, never-before-seen threats.
EDR solutions are constantly watching for unusual patterns on every device. If they spot something fishy, they can automatically quarantine a compromised laptop to stop an infection from spreading across your entire network. This proactive defense is absolutely essential for stopping modern nightmares like ransomware.
Securing Your Cloud Solutions
These days, most small to midsize businesses have a foot—or their whole body—in the cloud, using services like Microsoft 365 or Amazon Web Services. This creates a whole new perimeter that needs defending. In my experience, simple misconfigurations in cloud solutions are a top cause of major data breaches, making dedicated cloud security a non-negotiable layer.
Cloud Security Posture Management (CSPM) is the tool for this job. Think of it as your automated compliance officer for the cloud. It’s always scanning your cloud environments for common but dangerous security risks, such as:
-
Improper access controls that leave sensitive files open to the public internet.
-
Lack of encryption on stored data, making it useless if stolen.
-
Compliance violations with standards like HIPAA or PCI DSS.
CSPM tools give you a clear view of your cloud infrastructure, send alerts when something is wrong, and can often fix the issues for you automatically.
The Human Layer: Policies and Training
Finally, we get to the most unpredictable layer of any defense: your people. A staggering 82% of data breaches involve a human element, whether it's someone falling for a phishing email or just using "Password123" for everything. No amount of AI or cloud technology can fully solve the human factor.
This is exactly why security awareness training and strong internal policies form such a vital layer. This isn't just a one-and-done memo; it's an ongoing process that involves:
-
Establishing Clear Policies: You need written, enforced rules for password complexity, how to handle sensitive data, and using personal devices for work.
-
Conducting Regular Training: Teach employees how to spot phishing attempts, the risks of public Wi-Fi, and other common social engineering tricks.
-
Running Phishing Simulations: The best way to see if training is working is to test your team with controlled, fake phishing campaigns. It shows you exactly who needs a little more coaching.
By weaving these layers together—firewalls, EDR, cloud security, and a well-trained team—you create a defense that is resilient and overlapping. Honestly, it's the only way to effectively protect your business from the sheer variety of threats out there today.
Your Action Plan for Implementing Layered Security
Knowing what security layers you need is one thing. Actually putting them into practice without getting overwhelmed? That’s a whole different ballgame. I’ve seen countless small business owners get stuck in "analysis paralysis," staring at a long list of security tools and not knowing where to start.
The secret is to treat it like building a house. You don't start with the roof; you start with a solid foundation and build up from there. It’s about taking practical, logical steps that deliver the biggest impact first, rather than trying to do everything at once.

This process turns security theory into a real-world, resilient defense. It all begins with taking an honest look at where you stand right now.
Start with a Clear-Eyed Risk Assessment
Before you buy a single piece of software or hardware, you absolutely must understand what you’re trying to protect. This is the single most critical step, and it’s the one most small businesses skip—a mistake that often proves costly.
Think of a risk assessment as a thorough inspection of your digital property. You're systematically checking for unlocked doors, broken windows, and hidden vulnerabilities before a burglar has a chance to find them.
The process involves identifying your most valuable digital assets—like customer databases in your cloud CRM, financial records, or proprietary designs—and then figuring out the most likely ways those assets could be compromised. A proper assessment hands you a prioritized to-do list, showing you exactly where to focus your time and money for the biggest security wins.
Without a risk assessment, you're essentially spending your security budget blind. You might invest heavily in a new firewall while leaving your sensitive cloud solutions completely exposed. The assessment provides the map you need to invest smartly.
Deploy Foundational Tools and Controls
Once you have your risk assessment in hand, you can start putting up your defenses. This is where the plan becomes tangible protection. The order you do things in matters, as each layer builds on the one before it, creating a stronger, more integrated shield.
Here’s a practical, phased approach I recommend to our small and midsize business clients:
-
Lock Down Identities and Endpoints First: Your first move should always be securing your people and the devices they use. That means immediately rolling out Multi-Factor Authentication (MFA) across every possible account. At the same time, deploy a modern AI-powered Endpoint Detection and Response (EDR) solution to replace that outdated antivirus software on every company computer.
-
Fortify the Network Perimeter: With your people and devices secured, the next step is the front gate. Install and correctly configure a Next-Generation Firewall (NGFW). This acts as your primary gatekeeper, inspecting traffic and stopping threats before they can even get a foothold on your internal network.
-
Secure Your Cloud Presence: If you rely on cloud solutions like Microsoft 365 or Google Workspace, your next focus is locking them down. We use principles from Cloud Security Posture Management (CSPM) to find and fix the common misconfigurations that hackers love to exploit.
This structured rollout ensures you're tackling the most common attack vectors right away, which immediately lowers your overall risk profile.
Establish Non-Negotiable Security Routines
Technology can only do so much. The best cybersecurity solutions for businesses are built on consistent, repeatable processes. Once your foundational tools are in place, you need to create the daily, weekly, and monthly habits that keep your defenses sharp.
These are the routines that should be non-negotiable:
-
Consistent Data Backups: Don't just back up your data; do it right. Follow the 3-2-1 backup rule: keep three copies of your data, on two different types of media, with one copy stored securely off-site (often in a secure cloud solution). Most importantly, test your backups regularly to make sure you can actually restore them when you need to.
-
Systematic Patch Management: Create a formal process for applying security patches to all software—from operating systems to applications—as soon as they’re available. Unpatched software is one of the easiest ways for an attacker to walk right in.
-
Ongoing Employee Training: Security is not a one-and-done training session. You need to keep your team vigilant. Schedule regular security awareness refreshers and run simulated phishing campaigns to teach them how to spot the latest threats.
By turning these actions into ingrained habits, you build a culture of security that makes your technology infinitely more effective. This action plan gives you a clear path from understanding your risks to building a robust, layered defense that can adapt and grow right along with your business.
Finding the Right Cybersecurity Partner for Your Business
For most small to midsize businesses, trying to manage the tangled web of cybersecurity, AI tools, and cloud infrastructure in-house just isn't realistic. It's a full-time job, and frankly, you've got a business to run. The threats change by the minute, and keeping up requires a level of dedicated expertise that’s hard to come by.
This is where finding the right expert partner becomes one of the most important decisions you'll make. It’s not just about offloading tasks; it’s about bringing in a strategic ally who provides both the day-to-day technical muscle and the high-level guidance you need to stay resilient for the long haul.

Differentiating an MSP from a vCIO
First things first, let's clear up some jargon. You'll hear terms like MSP and vCIO thrown around, and while the services can overlap (and are often offered by the same firm), they fill two very different—and equally vital—roles for a small business.
I like to use a race car analogy. To win, you need both a pit crew and a race strategist. One can't succeed without the other.
-
The Managed Service Provider (MSP): This is your hands-on pit crew. They're the ones in the trenches every day, handling the technical heavy lifting. They’re monitoring your network, managing your firewall, responding to AI-driven security alerts, and making sure your cloud backups are solid. Their focus is on keeping the engine running smoothly and securely, right now.
-
The virtual Chief Information Officer (vCIO): This partner is your race strategist. They're looking at the whole track, analyzing the competition, and planning your route to victory. A vCIO helps you build a technology roadmap, align your IT budget and cloud strategy with your business goals, and ensures your cybersecurity investments are smart, scalable, and compliant.
A great partnership combines both. The MSP handles the immediate "how" of your security, while the vCIO answers the strategic "why," making sure your technology not only protects you today but also fuels your growth for years to come.
Your Checklist for Choosing the Right Partner
Not all providers are created equal. When you’re vetting potential partners for cybersecurity solutions for businesses, asking the right questions is critical. Picking a mismatched partner can be just as dangerous as having no partner at all.
Use this checklist to cut through the noise:
-
Proven Expertise with Modern Tools: Do they live and breathe today’s tech, like AI-driven EDR, next-gen firewalls, and secure cloud solutions? Ask for specific examples. How do they actually use these tools to protect clients like you?
-
A Clear Incident Response Plan: Don't wait for a disaster to find out their plan is a mess. Ask them to walk you through their step-by-step incident response protocol. What are their communication procedures? What are their guaranteed response times? Get it in writing.
-
Strong Client Testimonials and Case Studies: A good provider will be proud to share their wins. Look for testimonials from businesses similar to yours in size and industry. This is real-world proof they can deliver.
-
Scalability and Future-Proofing: Your business is going to grow, and your IT partner needs to be ready to grow with you. How do their cloud services and pricing scale? Do they have a forward-looking approach that anticipates future threats and new AI opportunities?
For businesses in our region, having a partner who gets the local landscape is a huge advantage. Understanding your specific challenges and opportunities is part of the job. To give you a clearer picture, we've put together a complete overview of our managed IT services designed for companies right here in Western PA and Eastern OH.
Choosing a partner is a major step. Finding one who truly understands your business goals is the key to a secure and successful future.
Decoding the True Cost and ROI of Cybersecurity
One of the most dangerous mistakes I see small business owners make is viewing cybersecurity as just another line item on the expense sheet. It's a fundamental misunderstanding of what’s at stake. This isn’t about buying software; it’s an investment in your company’s survival, its reputation, and its ability to grow using tools like AI and the cloud. Getting that perspective right is the first real step toward building a business that can weather any storm.
The numbers behind a solid security plan can feel intimidating, but they’re actually pretty straightforward. Pricing really boils down to tangible things like the number of employees and computers you need to protect, the complexity of your network, and the specific level of protection your cloud solutions require. A small shop might invest a few thousand dollars a month for a managed security package, while a midsize company with more intricate needs will see that figure scale up.
But focusing only on the upfront cost is like looking at just one piece of the puzzle. The real conversation, the one that matters to your bottom line, is about the powerful Return on Investment (ROI) that good security delivers.
Understanding the Financial Trade-Off
At its core, the ROI of cybersecurity is all about mitigating risk. Think of it this way: proactive security spending is a small, predictable operational expense. A data breach, on the other hand, is a catastrophic, unpredictable financial disaster waiting to happen.
The average cost of a breach for a small business isn't just a scary statistic; it can easily climb into the hundreds of thousands of dollars. These aren't abstract costs. They include:
-
Downtime and Lost Revenue: Every single minute your cloud systems are offline, you're not serving customers, and you're actively losing money.
-
Regulatory Fines: If you're in an industry like healthcare or finance, the penalties for non-compliance after a breach can be absolutely crippling.
-
Legal Fees: Lawsuits from customers, partners, and employees are an unfortunate but very real consequence of a data leak.
-
Brand Damage: This is the silent killer. Once customer trust is gone, it's incredibly hard to win back, and that loss can permanently damage your place in the market.
When you frame it like that, investing in cybersecurity solutions for businesses becomes a no-brainer. Paying a monthly fee for managed security and strategic guidance is a tiny fraction of what a single major incident would cost. To really get a handle on the numbers, I recommend digging into resources on understanding the ROI of cyber security investments—it helps put the tangible benefits into clear focus.
Global Spending Underscores the Value
Don't just take my word for it; look at where businesses are putting their money globally. The massive worldwide investment in cybersecurity tells the whole story. North America has long been the leader in both spending and innovation, making up more than a third of the entire global market in 2024.
Europe isn't far behind, projected to hit $55.98 billion in spending by 2025. And the Asia-Pacific region is growing faster than anywhere else, with giants like China and Japan expected to spend over $11 billion and $9 billion respectively by 2025. These figures prove that savvy businesses everywhere recognize proactive defense as a non-negotiable cost of doing business.
A well-structured cybersecurity budget isn't about preventing every single attack—that's impossible. It's about making your business an unprofitable and difficult target for attackers while ensuring you can get back on your feet quickly if the worst does happen. It’s the ultimate business continuity plan for the modern SMB.
In the end, it all comes down to a simple question: Can you afford not to invest in your security? The costs of proactive defense are predictable and manageable. The costs of a breach are anything but.
Your Cybersecurity Questions Answered
If you’re running a small or midsize business, you’ve probably got a lot of questions about cybersecurity. It’s a complicated topic. We’ve pulled together the most common questions we hear from business owners and answered them in a straightforward way, so you can feel confident in your next steps.
Are We Really a Target?
The short answer? Yes. One of the most dangerous myths floating around is that cybercriminals only chase after the big fish—the Fortune 500 companies. The reality is much different.
Attackers use automated tools that constantly scan the internet for any weakness, anywhere. It doesn't matter if you have five employees or five thousand. In fact, small businesses are often seen as easier targets precisely because they tend to have fewer defenses in place. A breach can cause devastating financial and reputational damage, making proactive cybersecurity solutions for businesses a critical investment in your company’s future.
What Is the Most Important First Step?
Look, the end goal is always a complete, layered defense. But if you’re looking for the single biggest bang for your buck right out of the gate, focus on securing your user identities and your devices. It’s where you’ll see the biggest immediate reduction in risk.
Here’s how to do it:
-
Roll out Multi-Factor Authentication (MFA) on every single account you can, especially for your cloud solutions. This is your best defense against stolen passwords.
-
Get a modern, AI-powered Endpoint Detection and Response (EDR) solution on all your computers and servers. This is the software that actively protects the machines where your team gets their work done.
These two steps slam the door on the most common ways attackers break into a network.
How Does AI Actually Help with Security?
AI takes your defenses from old-school to next-generation. In the past, antivirus software relied on a list of known, previously identified viruses. It was purely reactive.
AI-powered security tools are different. They analyze behavior in real-time to spot activity that looks suspicious, flagging new and advanced threats that have never been seen before.
Think of it this way: traditional antivirus is like a security guard with a photo album of known criminals. AI is like a behavioral profiler who can spot a threat just by how they act, even if their face isn't in the album.
This is how modern security tools can detect a brand-new type of ransomware or notice when an employee’s account starts acting strangely within your cloud environment, stopping an attack before it can do real damage.
Is the Cloud More or Less Secure?
This is a great question. A cloud solution can be far more secure than anything you could build in your office, but that security is a shared responsibility. The big players like Microsoft Azure and Amazon Web Services operate with world-class security infrastructure that is simply out of reach for most small businesses.
However—and this is a big "however"—you are responsible for configuring your cloud environment correctly. A simple misconfiguration, an unchecked box, can leave your most sensitive data wide open to the internet. Working with an expert partner ensures your cloud setup is properly locked down and constantly monitored, giving you the best of both worlds: top-tier infrastructure and rock-solid configuration.
Ready to move from questions to a clear action plan? The team at Eagle Point Technology Solutions provides the expertise and layered security your business needs to operate with confidence. Let’s build your defense together.