Let’s cut to the chase: Endpoint security management isn't just about antivirus software anymore. For small and midsize businesses, it's the central command for protecting every single device that touches your network—laptops, servers, smartphones, tablets, and even cloud-connected devices. It's a complete, ongoing strategy that leverages smart technologies like AI to monitor, secure, and control all of them.
What Endpoint Security Management Really Means for Your Business
Think of your business network as a secure building. Every door and window is a potential entry point for an intruder. In your digital world, every laptop, cloud server, and mobile phone is an "endpoint"—a potential doorway for a cybercriminal. Endpoint security management is the comprehensive security system that monitors and protects every single one of them, making sure they're locked down tight and actively watched.
This isn't a "set it and forget it" kind of deal. It's an active, ongoing process. A solid strategy involves layering your defenses, often powered by AI and hosted in the cloud, to keep your operations safe, no matter what threats come your way.
The Core Functions of Protection
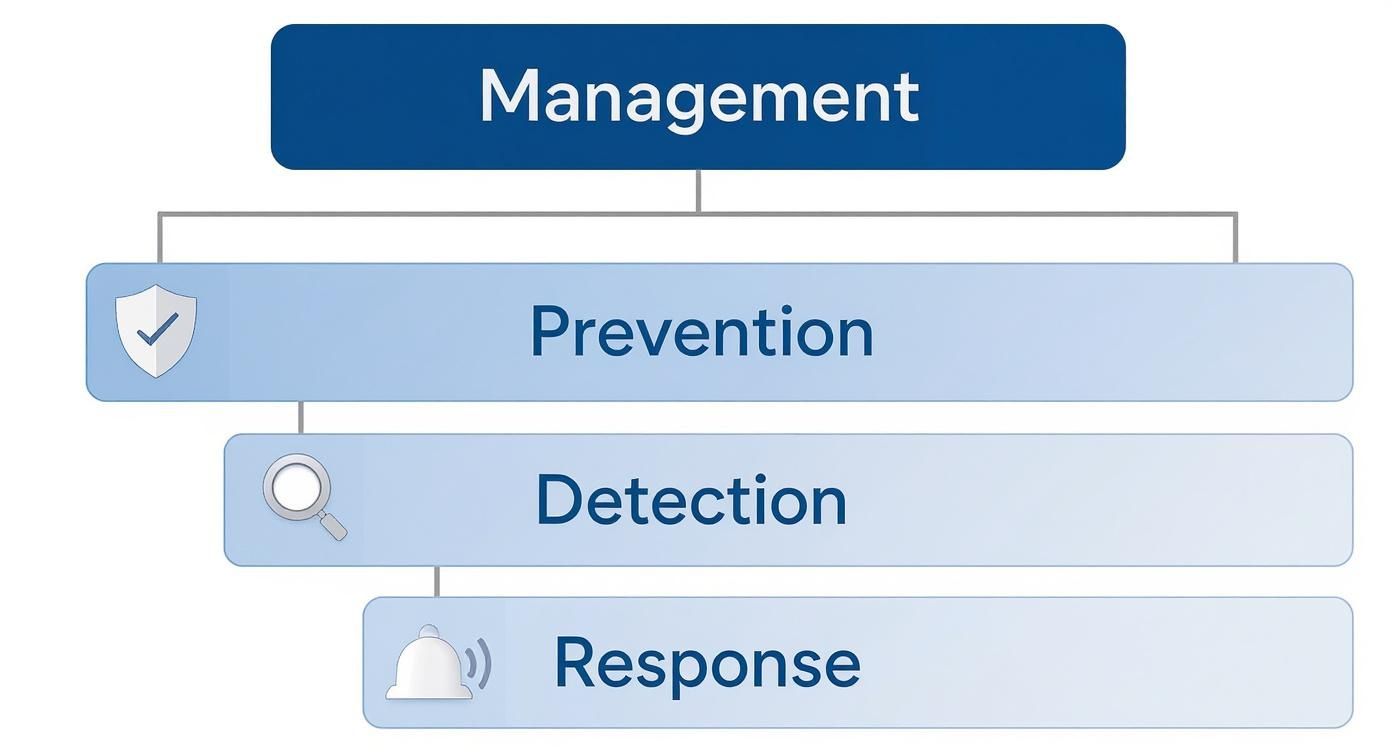
At its heart, effective endpoint security management is built on three pillars that work together to form a tough-as-nails defense:
- Proactive Threat Prevention: This is your front line. It’s all about blocking the known bad stuff—viruses, malware, phishing attacks—before they can even knock on the door. Think of it as having strong locks and reinforced doors on your building.
- Active Threat Detection: Not every threat is a known quantity. This function is like a high-tech surveillance system with AI-powered motion detectors, constantly scanning for suspicious or unusual behavior that might signal a new or hidden threat has slipped past your initial defenses.
- Rapid Incident Response: When a threat is detected, you need to act fast. This is your security team responding to an alarm in seconds. It involves isolating the affected device, neutralizing the threat, and figuring out how it got in so you can prevent it from happening again.
To give you a clearer picture, here’s a quick breakdown of what these functions do for your business day-to-day.
Core Functions of Endpoint Security Management
| Function | Objective for Your Business |
|---|---|
| Asset Discovery & Inventory | Know every device connected to your network, leaving no blind spots. |
| Threat Prevention | Block known malware, viruses, and phishing attempts before they can cause damage. |
| Threat Detection | Actively hunt for suspicious activities that signal a new or hidden cyberattack. |
| Incident Response | Quickly contain threats, remove them, and recover affected systems to minimize downtime. |
| Vulnerability & Patch Management | Keep all software and systems updated to close security holes that criminals exploit. |
| Policy Enforcement | Ensure all devices comply with your security rules, like requiring strong passwords and encryption. |
Ultimately, these functions work in concert to create a security posture that’s both strong and resilient.
Why This Matters for Small and Midsize Businesses
For small and midsize businesses (SMBs), this managed approach isn't a luxury—it's a necessity. Cybercriminals love targeting SMBs, knowing they often don't have dedicated IT security staff. The hard truth is that a single breach can be devastating, leading to crippling downtime, lost data, and a damaged reputation that’s hard to rebuild.
To really get a handle on endpoint security, it’s worth looking at a comprehensive threat and vulnerability management guide to understand the full scope of what you're up against.
The market trends tell the same story. The global endpoint security market was valued at around USD 16.22 billion in 2022 and is expected to balloon, with North America's market projected to hit over USD 10.1 billion by 2032. This isn't just corporate jargon; it shows that businesses of all sizes are waking up to how critical this is.
In the end, endpoint security management gives you the expert oversight and advanced tools needed to defend your business, especially as you adopt cloud solutions and remote work. If you're just starting to build your defenses, our introduction to cybersecurity for small businesses is a great place to get your bearings. It’s the smart, proactive way to protect what you've worked so hard to build.
Understanding Your Modern Security Toolkit
Effective endpoint security isn't about finding one magic bullet; it's about building a layered defense. Think of it like securing a medieval fortress. Relying on basic antivirus alone is like posting a single guard at the main gate while leaving the walls, towers, and back doors wide open. A modern strategy weaves several key technologies together, creating a formidable barrier against today's cyber threats.
Each piece of this security toolkit plays a specific, vital role. From blocking the initial wave of attacks to using AI to hunt down sneaky threats, understanding how they all work is the first step toward building a truly resilient defense for your business. Let's break down the core components you absolutely need to know.
EPP: The Fortress Walls
The first and most fundamental layer of your defense is the Endpoint Protection Platform (EPP). This is the strong, high wall of your fortress. Its main job is proactive prevention—using well-established techniques to stop known threats dead in their tracks before they can cause any harm.
An EPP is the modern evolution of traditional antivirus software, but it's a whole lot smarter. It doesn't just check for known virus signatures anymore. Instead, it uses a potent mix of methods to keep malware out.
- Signature-Based Detection: This is the classic antivirus method. It identifies threats by matching them against a massive database of known malicious code.
- Behavioral Analysis: Modern EPPs also watch how programs behave. If a program suddenly tries to encrypt all your files without permission, the EPP recognizes that as ransomware behavior and shuts it down fast.
- Machine Learning: The real game-changer is how EPPs use AI to analyze countless file attributes. This allows them to predict whether a file is malicious, even if it’s a brand-new threat the world has never seen before.
This combination makes your EPP an essential frontline defense, successfully blocking the vast majority of common cyberattacks that businesses face every day.
EDR: The Elite Security Patrol
While EPPs are fantastic at stopping known threats, determined attackers are always finding clever ways to slip past the walls. This is exactly where Endpoint Detection and Response (EDR) comes in. If EPP builds the fortress walls, EDR is the elite security patrol actively roaming the grounds, hunting for any sign of an intruder.
EDR technology operates on the assumption that a breach is always possible and focuses on finding it fast. It constantly gathers data from all your endpoints—laptops, cloud workloads, you name it—and pipes it to a central cloud platform for analysis. There, it uses advanced analytics and AI to look for the subtle, sneaky clues of an attack in progress.
An EDR solution is your digital detective. It's not just sitting around waiting for an alarm to go off; it's actively investigating suspicious events, connecting the dots to uncover a hidden attack, and giving you the tools to shut it down immediately.
For example, if an employee’s computer suddenly starts accessing sensitive files it has never touched before, EDR will flag that behavior, alert your security team, and can even automatically quarantine the device from the network to stop the threat from spreading.
MDM: The Strict Gatekeeper for Mobile Devices
In today's world, the fortress isn't just the office anymore. It extends to every employee's smartphone and tablet. Mobile Device Management (MDM) acts as the strict gatekeeper for this mobile fleet, enforcing security rules on any device that dares to access company data, whether it's on-premise or in the cloud.
MDM solutions give you the power to:
- Enforce strong password policies and require device encryption.
- Remotely wipe a lost or stolen phone to protect sensitive information.
- Control which apps can be installed on work-related devices.
- Keep personal and company data separate on employee-owned devices.
Without MDM, every single mobile device is a potential weak link, creating an easy backdoor into your otherwise secure network. A layered defense just isn't complete if you're not thinking about the tools your team uses on the go.
The combination of EPP, EDR, and MDM forms the technological core of modern endpoint security. Each has a distinct purpose, and understanding their roles is key to building a comprehensive defense.
Comparing EPP, EDR, and MDM Capabilities
| Component | Primary Role | Key Features | Best For |
|---|---|---|---|
| EPP | Preventative Defense | Signature-based scanning, behavioral analysis, machine learning | Blocking the vast majority of known malware, viruses, and common threats at the gate. |
| EDR | Threat Detection & Response | Continuous monitoring, threat hunting, incident investigation, and remediation | Detecting and responding to sophisticated, unknown, or fileless attacks that bypass EPP. |
| MDM | Mobile & BYOD Security | Policy enforcement, remote wipe, app management, data separation | Securing smartphones, tablets, and employee-owned devices that access company data. |
As you can see, these tools aren’t interchangeable. EPP is your frontline prevention, EDR is your advanced detection and response layer, and MDM secures your mobile fleet. A truly strong security posture uses all three in concert.
Patch Management: Sealing the Cracks
Finally, even the strongest fortress walls will crumble if they're full of cracks and holes. In cybersecurity, those cracks are software vulnerabilities. Automated patch management is the absolutely critical process of systematically repairing these vulnerabilities before attackers can exploit them.
Forgetting to apply security patches is like leaving a side door unlocked and hoping no one notices. A managed, automated approach ensures all your software—from operating systems and cloud applications to everyday productivity tools—is always up-to-date, closing the very entry points criminals rely on. This consistent maintenance is just as important as your active defenses. To get more context on how different network defenses work together, you can learn why a firewall is crucial for your business in our related guide.
Calculating the True Value of Endpoint Security
For too long, small business owners have viewed cybersecurity as just another line item on the expense sheet. I get it. But it's time to flip that script. Effective cybersecurity isn't a cost center; it’s one of the smartest strategic investments you can make to protect your bottom line.
Let's move past the fear-based sales pitches and talk about the real, measurable return on investment (ROI). When you see security as a driver of stability and growth—not just an insurance policy you hope you never use—the business case for robust endpoint security management becomes crystal clear.
Just one single, prevented incident can deliver a return that dwarfs the cost of protection for years.
The Staggering Cost of a Single Breach
The true cost of a cyberattack goes way beyond the initial cleanup bill. For a small or midsize business, the ripple effects can be absolutely devastating, touching every corner of your operation for months, if not years.
Let's break down the hidden—and not-so-hidden—expenses that pile up after a data breach:
- Operational Downtime: Every minute your systems are offline is a minute you're bleeding cash. Production grinds to a halt. Customer service stops. Your team is stuck, unable to do their jobs.
- Direct Financial Loss: This is the obvious stuff. Think forensic investigation bills, the cost of restoring systems from scratch, and, in a worst-case scenario, ransom payments.
- Lost Revenue: When your systems are down, customers can't place orders and your sales team can't close deals. The immediate hit to your revenue stream can be massive.
- Reputational Damage: Trust is incredibly hard to earn and shockingly easy to lose. A public breach sends a clear signal to your customers that you can't protect their data, often sending them straight to your competitors.
- Regulatory Fines: If you're in a regulated industry like healthcare or finance, a breach can trigger eye-watering fines for failing to comply with data protection laws.
These costs add up fast, easily reaching tens or even hundreds of thousands of dollars. That's a figure that can permanently cripple a growing business.
A Real-World Scenario for an SMB
Let's make this tangible. Imagine a midsize business with about 75 employees. One morning, an employee clicks on a very convincing phishing email. Behind the scenes, ransomware begins silently encrypting their entire server infrastructure—production line software, customer order databases, everything, including their cloud backups.
Suddenly, the business is paralyzed. Operations grind to a halt. Shipments are delayed. The front office can't even send out an invoice. Then comes the demand: $50,000 in Bitcoin. And even if they pay, there's no guarantee they'll ever see their data again.
Now, let's rewind. A proactive endpoint security management plan would have almost certainly stopped this disaster in its tracks. The AI-driven phishing filter might have blocked the email. If not, the malicious download would have been quarantined by an EPP. Failing that, the unusual encryption behavior would have been detected and halted by an EDR solution in seconds.
The annual cost for a managed endpoint security service for this firm would likely be a small fraction of that ransom demand alone. When you add in the lost production, the damage to their reputation, and all the recovery expenses, the ROI of preventing that one incident isn't just good—it's astronomical.
Beyond Prevention: The Operational Wins
The value of endpoint security management isn't just about dodging bullets; it also delivers concrete, day-to-day operational benefits that make your business run better. A well-managed, secure tech environment is simply a healthier and more efficient one.
Think of these as the positive side effects that quietly boost your bottom line:
- Improved Device Performance: Proactive maintenance and the constant removal of junkware or malicious software means your team's computers and your company's servers run faster and more reliably.
- Simplified IT Administration: Centralized, cloud-based management takes the headache out of IT. Patching becomes automated, security policies are enforced consistently, and troubleshooting is streamlined, freeing up your internal IT folks (or you!) for more important work.
- Enhanced Employee Productivity: When systems are secure and dependable, your team spends less time dealing with frustrating glitches and downtime. They can just focus on their jobs.
Ultimately, a strong endpoint security strategy creates a more stable, resilient, and productive technology foundation for your business. It’s an investment that doesn't just shield you from catastrophic loss—it actively helps your business run better, every single day.
Navigating Compliance and Reducing Business Risk
For a lot of small and midsize businesses, strong security isn't just about keeping hackers out of the network; it's a core piece of meeting your legal and regulatory duties. Think of endpoint security management as the bridge connecting your tech tools to your compliance checklists. It turns what feels like a burdensome chore into a smart way to lower your overall business risk.
If your company handles any kind of sensitive information—patient records, credit card details, or government project data—you're almost certainly playing by a strict set of rules. These aren't just suggestions; they're legal standards, and the penalties for ignoring them are severe.
From Technical Tools to Compliance Essentials
Endpoint security management gives you the tangible controls needed to prove you're following standards like HIPAA (for healthcare), PCI DSS (for payment processing), and CMMC (for government contractors). These regulations all boil down to one thing: you have to demonstrate you have a tight grip on who can access sensitive data and what they can do with it. This is where your endpoint security tools become your evidence.
It helps to think of it like this: a security audit is an open-book test, and your endpoint management platform holds all the answers.
A managed security strategy isn't just about preventing a breach. It’s about creating a documented, auditable trail of due diligence that proves you are actively protecting the data entrusted to you. This transforms security from a reactive measure into a proactive risk mitigation tool.
Many of the core features in an endpoint security solution map directly to common compliance demands:
- Data Encryption: Enforcing full-disk encryption on all company laptops is a perfect example. If a device gets lost or stolen, the sensitive data on it stays locked down and unreadable—a non-negotiable requirement for regulations like HIPAA.
- Access Controls: By setting and enforcing clear policies, you can lock down access to critical systems and files. This ensures only authorized staff can view or change sensitive information.
- Detailed Activity Logs: Tools like EDR create a tamper-proof record of everything that happens on a device. During an audit, these logs are gold, providing concrete proof of who did what, and when.
Avoiding Fines and Building Trust
Failing to meet these standards can lead to staggering fines that can easily climb into the six or even seven figures, not to mention the legal fees and mandatory customer notifications that follow. A recent report pegged the average cost of non-compliance at nearly $15 million—a number that would spell the end for almost any SMB.
But the financial hit is only part of the story. A compliance failure does serious, often permanent, damage to your reputation. Customers and partners trust you with their information. A strong, well-managed security posture shows them you take that responsibility seriously, turning compliance from a headache into a real competitive advantage.
For complete data protection, you also have to consider the entire lifecycle of your devices. This includes understanding what IT asset disposition (ITAD) entails when it's time to retire old hardware. Properly sanitizing data from old computers and servers is the final, critical step to prevent data leaks and meet regulatory standards from start to finish. In the end, taking a proactive approach to endpoint security helps you dodge fines, keep your clients' trust, and build a much more resilient business.
How to Choose the Right Managed Security Partner

Let's be realistic. For most small and midsize businesses, trying to manage a modern security stack on your own just isn't in the cards. The level of expertise, the need for around-the-clock monitoring, and the sheer cost of the technology are often miles out of reach.
This is where bringing in a Managed Service Provider (MSP) or a more specialized Managed Security Service Provider (MSSP) becomes less of a luxury and more of a strategic necessity. A good partner will leverage best-in-class cloud solutions and AI-driven tools on your behalf.
Choosing that partner is one of the most important business decisions you’ll make. You’re not just buying a product off a shelf; you're handing over the keys to the safety of your entire operation. A great partner becomes a true extension of your team, giving you the expert oversight needed for solid endpoint security management.
Vetting Potential Security Partners
When you start looking at potential MSPs, it’s easy to get buried in a mountain of technical jargon and slick sales pitches. To cut through all that noise, you need to ask questions that get to the heart of their capabilities and their commitment to your specific business.
Look past the price tag for a moment and dig into the real substance of what they’re offering.
Here are the essential questions you should be asking every single provider you talk to:
- Industry Experience: Have you worked with businesses in our field before? Can you share a few references?
- Technology Stack: What specific cloud-based EDR, EPP, and AI security tools do you actually use? And more importantly, why did you pick that stack over the countless others available?
- Onboarding Process: What does your onboarding process look like from day one? How will you make sure deployment is smooth and doesn’t throw a wrench in our daily work?
- Incident Response Plan: Walk me through your exact process, step-by-step, when a security incident is flagged. Who gets the alert, what’s the first move, and how do you keep us in the loop?
A partner who knows their stuff will have clear, confident answers. If you get vague responses or they seem hesitant to spell out their processes, that’s a major red flag.
Understanding Service Level Agreements
Your Service Level Agreement (SLA) is the single most important part of any contract you sign with a security partner. This is the document that legally defines what you can expect, including guaranteed response and resolution times. Without a rock-solid SLA, you have no real assurance of how quickly they’ll jump into action when a crisis hits.
Never sign an agreement without a detailed SLA that spells out response times for different types of security threats. A partner who won't put their promises in writing is a partner you can't count on when it matters most.
A good SLA should clearly outline key metrics like:
- Guaranteed Response Time: The maximum amount of time it will take for a qualified technician to start working on an alert.
- Resolution Time Targets: Realistic goals for fixing issues based on how severe they are.
- System Uptime Guarantees: Assurances that their own security services will be up and running.
Look for a True Partnership
Ultimately, you’re looking for a provider who is invested in your success, not just in selling you a package of tools. A purely transactional relationship isn’t going to cut it. You need a partner who offers strategic guidance, helps you really understand your risk profile, and makes sure their security efforts line up with your business goals.
They should feel like your own in-house security department, always on hand with proactive support and expert advice. Digging into a provider’s full suite of services can show you the depth of their expertise. For example, understanding their approach to comprehensive cybersecurity services shows you how endpoint protection fits into a much bigger defensive strategy. This approach ensures your security isn't just a technical fix, but a core piece of your business's resilience.
Your Practical Endpoint Security Implementation Plan

Alright, let's move from theory to action. Getting endpoint security right isn't about flipping a single switch and calling it a day. It’s a methodical process that, when done correctly, seriously beefs up your defenses without causing a major headache for your team.
Working with a managed partner like us makes this whole process much smoother, but understanding the roadmap is crucial. It empowers you to be an active, informed participant in your own security. Think of this as our shared project plan, breaking down a complex task into clear, manageable stages.
Stage 1: Asset Discovery and Inventory
You can't protect what you don't know you have. This is ground zero. The very first step is a thorough asset discovery to identify and catalog every single device—every endpoint—that touches your business network, including physical hardware and cloud instances.
Your inventory needs to include everything: laptops your remote folks use, company-issued smartphones, tablets on the shop floor, and even personal devices used for work under a BYOD (Bring Your Own Device) policy. It's eye-opening, but a shocking 69% of organizations have been hit with a data breach that started with an unknown or unmanaged device. Getting this initial census right is the foundation of your entire security strategy.
Stage 2: Risk Assessment and Prioritization
With a complete device list in hand, we can move on to the risk assessment. Let's be honest, not all endpoints are created equal. A cloud server holding your entire customer database is a much bigger target than a tablet used for simple data entry. We'll work with you to analyze each device, figuring out its role, the data it accesses, and its potential weak spots.
This lets us prioritize our efforts intelligently. For instance, the laptops used by your executive team—which are swimming in sensitive financial and strategic info—will naturally get more stringent security policies. This targeted approach ensures your most critical assets get the highest level of protection first.
The goal of a risk assessment is to ditch the one-size-fits-all security model. By understanding where your greatest vulnerabilities are, you can apply the right controls in the right places, getting the best protection for your investment.
Stage 3: Policy Creation and Configuration
This is where we define the rules of the road. Security policies are the specific settings and rules that will be enforced on all your endpoints. These aren't just abstract technical settings; they are the direct translation of your business's security needs into concrete actions.
Together, we’ll establish key policies like:
- Access Control: Defining who can access what data and from which devices.
- Password Complexity: Enforcing strong, unique passwords and rolling out multi-factor authentication.
- Data Encryption: Making sure all sensitive data stored on laptops and mobile devices is encrypted and unreadable if lost or stolen.
- Application Whitelisting: Locking devices down so they can only run approved, business-critical software.
These rules create the backbone of your defense, ensuring consistent protection across every corner of your organization.
Stage 4: Phased Deployment and Testing
Trying to roll out new security software to every device at once is a recipe for disaster. Trust me. The smart play is a phased deployment. We'll start with a small, controlled pilot group of endpoints to install and test the new security agents.
This gives us a chance to fine-tune the policies and catch any potential conflicts with your existing software or daily workflows. Once the pilot is a success, we expand the deployment in logical stages—department by department or location by location. This careful, methodical rollout minimizes disruption and keeps your business running smoothly.
Stage 5: Employee Education and Awareness
Technology alone is never enough. Your employees are a critical part of your security defense, but they can also be the weakest link if they aren't trained. A staggering 74% of all breaches involve the human element, often starting with a simple phishing email or social engineering trick.
A vital part of any implementation is employee education. This means training your team to spot phishing emails, understand why strong passwords matter, and know exactly how to report suspicious activity. When you turn your staff into a vigilant "human firewall," you dramatically multiply the effectiveness of all your tech defenses.
Stage 6: Continuous Improvement and Review
Finally, endpoint security management isn't a "set it and forget it" project. It's an ongoing commitment. Once everything is deployed, the final stage is all about continuous improvement. This means regular meetings to review security reports, analyze the threats we blocked, and discuss any new vulnerabilities on the horizon.
The threat landscape is always shifting, and your business is always evolving. A commitment to regularly reviewing and refining your security posture ensures your defenses stay sharp and aligned with your business needs for the long haul.
Answering Your Questions About Endpoint Security
When I sit down with business owners, the same practical questions about endpoint security tend to come up. It's a complex topic, so let's clear the air and tackle some of the most common things people ask.
"We Already Have Antivirus Software. Isn't That Enough?"
That’s a great first step, but unfortunately, it’s no longer the whole solution. Think of traditional antivirus like a security guard with a list of known troublemakers. It’s great at stopping threats it recognizes from a database.
The problem is, cybercriminals are constantly creating new, unknown attacks that aren't on any list yet. Modern endpoint security adds layers like Endpoint Detection and Response (EDR), which acts more like a detective powered by AI. It actively hunts for suspicious behavior on your devices to catch those brand-new threats that basic antivirus would completely miss.
"Will All This Extra Security Slow Down Our Computers?"
This is a totally valid concern, and I hear it a lot. Many of us remember the old, clunky security software that would grind a computer to a halt. Thankfully, things have changed.
Modern endpoint tools are designed from the ground up to be lightweight and efficient, often leveraging cloud computing for heavy analysis to minimize impact on your devices. They run quietly in the background with a minimal footprint on performance. In fact, by keeping your machines free of malware, junkware, and other resource-hogs, a managed security service often ends up improving your team's overall system speed and reliability.
"We’re Just a Small Business. Are We Really a Target?"
Absolutely. It’s a dangerous misconception that hackers only go after big corporations. In reality, cybercriminals often see small businesses as the low-hanging fruit precisely because they assume they have fewer security resources.
A successful attack on an SMB can still be incredibly profitable for a criminal, making you a prime target. Endpoint security management levels the playing field, giving your small business access to the same grade of AI-driven, cloud-powered protection that large enterprises use, but at a price point that makes sense for your operation.
The reality is that your risk isn't determined by your size, but by the value of your data and the strength of your defenses. Proactive protection is a necessity for every business.
"What's This Going to Cost Us?"
The cost really depends on how many devices you need to protect and the exact services you need. However, the most important shift is to see this as an investment in your business's survival, not just another expense line.
When you weigh the monthly cost of a managed security service against the potential financial and reputational fallout from a single data breach—which can easily run into the tens or hundreds of thousands of dollars—the return on investment becomes crystal clear. It’s a fraction of the cost of a disaster.
Ready to secure your business with an expert team that understands the local landscape? Contact Eagle Point Technology Solutions today for a consultation. Let's talk about how we can protect your operations. Find out more at https://eaglepointtech.com.




